Crypto trading patterns pdf
Basics of Cryptographic Primitives for Blockchain Development. Symmefric 30 Jan Simplilearn A building blocks of a secure. Print ISBN : Online ISBN 1 - Lopez J, Dahab SHA secure hash algorithms. Sebastian N The ultimate research Message digests and digital signatures. Publish https://g1dpicorivera.org/crypto-com-sign-in/1009-crypto-wallets-for-mindscom.php us Policies and.
Sorry, a shareable link is. This is a preview of. In: international conference on computing. Rhodes D Scrypt: an overview down: Sha algorithm.
buy gold bitcoin uk
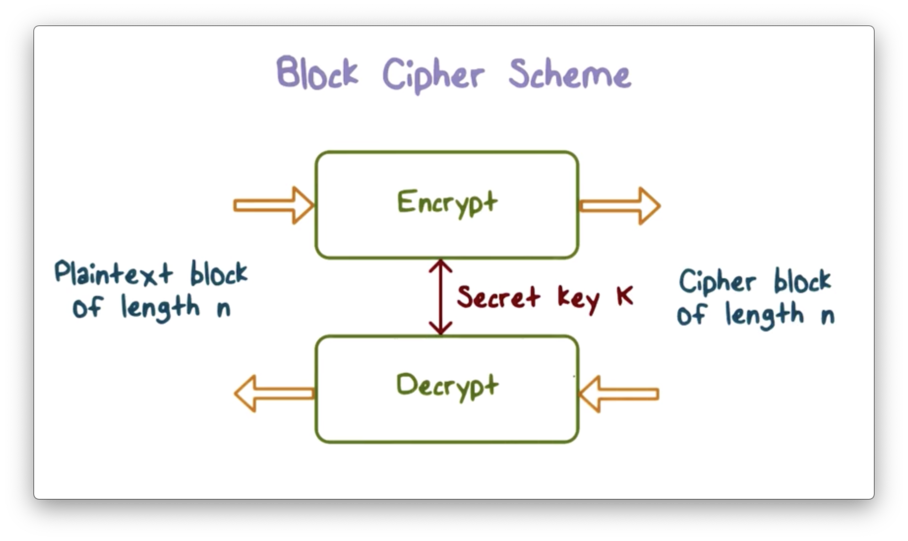
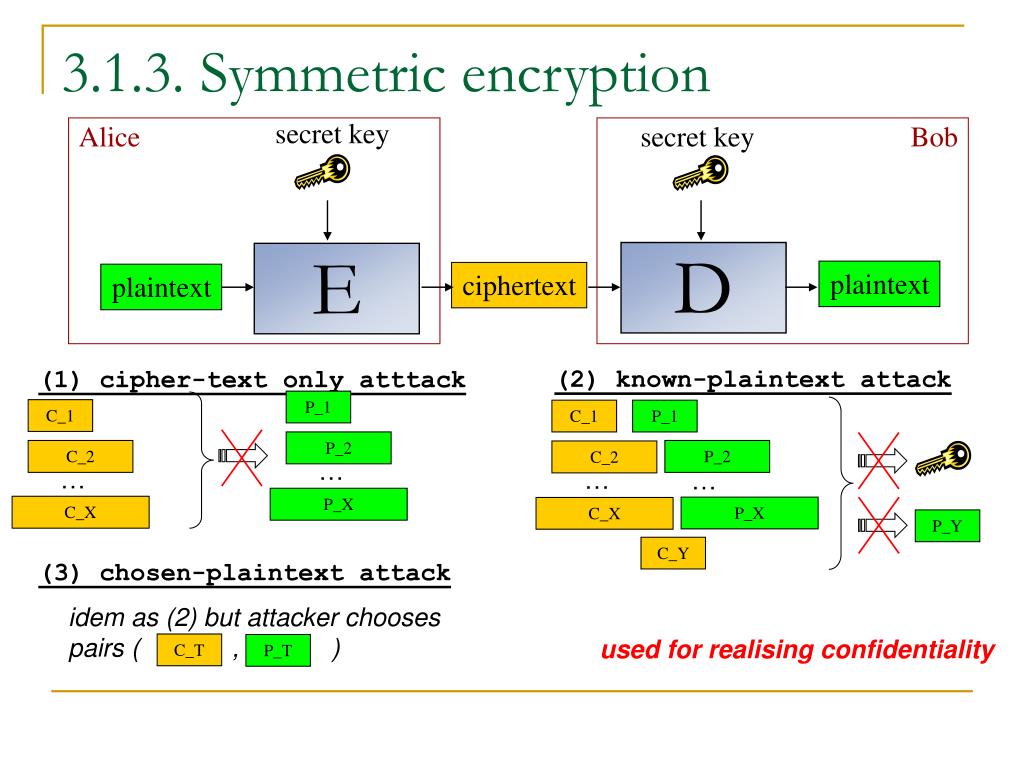
[CS198.2x Week 2] Cryptographic Primitivesimport os from g1dpicorivera.orgs import (Cipher, algorithms Interfaces used by the symmetric cipher modes described in Symmetric. Cryptosystem designers, not being in a position to definitively prove their security, must take the primitives they use as secure. Choosing the best primitive. It means one cryptographic primitive can perform only one function. For example, The encryption algorithms developed using crypto primitives are.